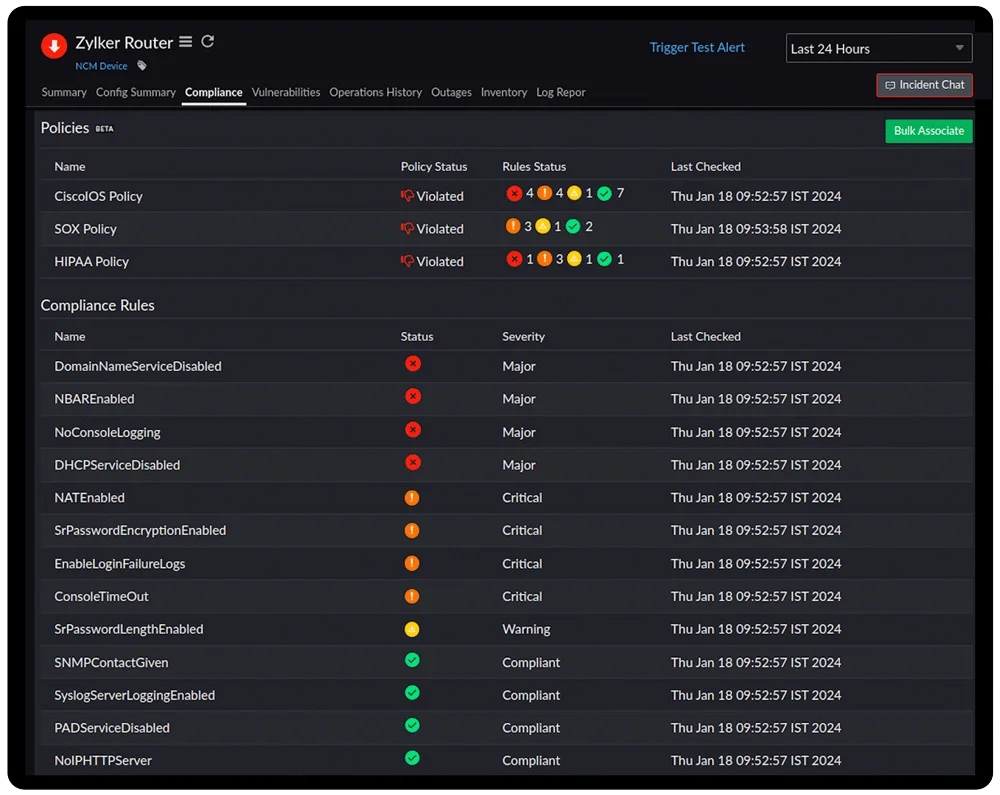
What is network configuration compliance?
Adhering to industry standards like Cisco IOS, SOX, HIPAA, or the PCI DSS and any other custom organizational policies protects your networks against threats. However, implementing network compliance management manually is impractical and often impossible due to the complexity and fluctuating structures of organizational networks.
By using an automated network configuration compliance system, network administrators can easily monitor all of their network devices and make sure they're following the necessary rules and policies. If any devices are not compliant, you can quickly identify them on a single pane and take the steps needed to prevent any network outages.
Why do you need network configuration compliance?
Properly configured networks contribute to efficient operations. Compliance ensures that devices work together seamlessly, reducing the likelihood of errors, downtime, and the associated costs.
Complex networks and ever-evolving threats have made manual network configuration compliance impossible.
Managing network devices from different vendors is an overwhelming task.
Noncompliance with industry standards can lead to costly, risky consequences for organizations.
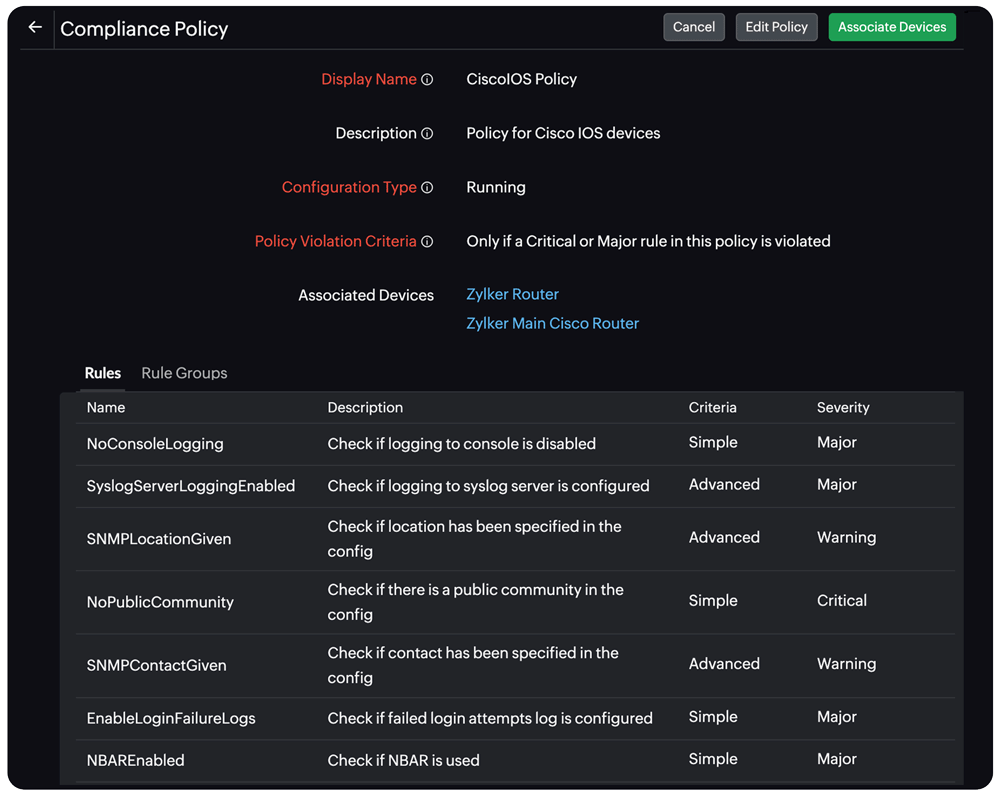
Achieving network compliance with Site24x7
Site24x7 has got your back when it comes to meeting compliance requirements like Cisco IOS, SOX, HIPAA, the PCI DSS, and your own organization-specific policies. The best part? With our user-friendly interface, ensuring all your policies are met is an absolute breeze. No more stress, just pure peace of mind!
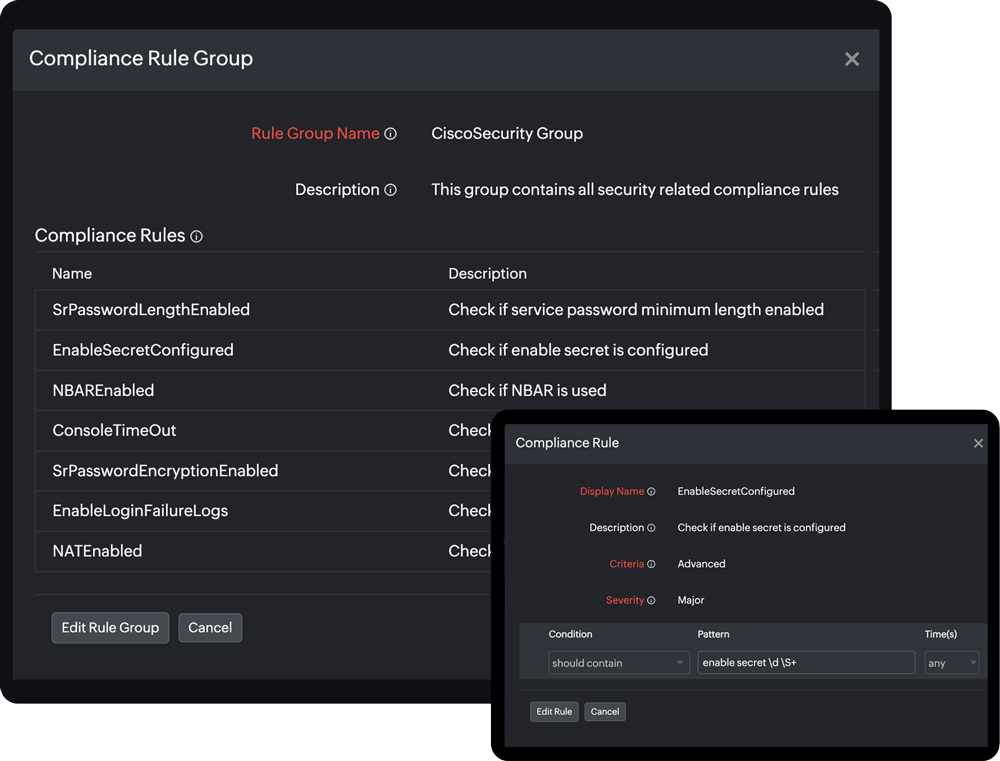
How does network configuration compliance work?
Our NCM tool automatically backs up device configurations when a change is detected and performs a compliance check to make sure every component is properly configured and compliant. If it detects any noncompliance based on established policies, you'll receive an alert based on the threshold conditions you've set.
So please sit back, relax, and let our NCM tool do the hard work for you!
An overview of network configuration compliance
1. Why is network configuration compliance important?
Network configuration compliance is of utmost importance for several reasons:
Security
Organizations can minimize the likelihood of security breaches and unauthorized access to their network by adhering to compliance standards.
Stability and reliability
Configuring network devices properly is crucial for the optimal, efficient functioning of networks with minimal downtime. Consistency in configuration also aids in troubleshooting and problem resolution.
Improved interoperability and compatibility
Maintaining industry standards allows devices to communicate and work together seamlessly, which is crucial in complex networks with interconnected devices and technologies. Compliance ensures that devices can exchange information and function properly without any conflicts or disruptions.
Legal requirements
Many industries, such as banking and healthcare, have specific guidelines and regulations on network security and data protection. To avoid legal penalties, reputational damage, and potential lawsuits, organizations must ensure compliance with these standards.
By prioritizing compliance, organizations can safeguard their network infrastructure and maintain a secure, reliable network environment.
2. What are the best practices for achieving network compliance?
To achieve network compliance, organizations must have a comprehensive network configuration management policy, regularly monitor and audit their network, manage vulnerabilities, and train employees. These best practices ensure the network's integrity, confidentiality, and availability as well as compliance with regulations and industry standards.
To achieve network compliance:
Evaluate compliance requirements
An organization must follow external compliance rules set by regulators and internal compliance rules that it establishes for itself. For both reasons, carefully identifying and evaluating the compliance mandates that the business must meet and determining what their implications are for network operations and security are critical first steps in network compliance.
Enforce the necessary network controls
Network administrators must decide which specific network configurations are needed to meet the requirements established in the first step and must enforce them across all devices.
Monitor and audit the network
Network monitoring data reflects the actual state of the network, as opposed to the expected behavior. So, constantly monitoring networks provides up-to-date information that verifies whether the device configurations comply with the regulations.
3. What are the benefits of achieving network compliance?
Improved security
Adhering to compliance standards ensures that your networks stay secure from emerging threats.
Increased customer trust
If customers are confident that their data is protected from hackers, they are more likely to remain loyal to your organization over an extended period.
Rising revenue
As your customer base grows, your revenue will consistently improve.
Reduced losses from outages
Achieving network compliance prevents financial losses caused by outages as well as penalties imposed for noncompliance.
A competitive advantage
Enforcing strict compliance policies can give you a competitive advantage over those who don't do the same.