Policies and permissions
Whether you are providing access by creating an IAM user or via the cross-account IAM role, you need to provide permissions for Site24x7. These permissions decide what specific AWS resources can be accessed.
Site24x7 requires ReadOnly permissions to your AWS services and resources. You can either assign the default ReadOnly policy, assign our custom policy, or create your own.
Default ReadOnly access policy (recommended)
To ensure that there are no performance blind spots, and to make use of Site24x7’s full scope of monitoring capabilities, we highly recommend you to assign the default ReadOnly policy document to the IAM user/Role created. This policy provides full read-only access to all popular AWS services.
- Currently the read-only permissions required to monitor Kinesis Video stream usage are not present in the managed policy "ReadOnlyAccess". To monitor you can either apply the managed policy "AmazonKinesisVideoStreamsReadOnlyAccess" along with the "ReadOnlyAccess" policy or construct a new policy from scratch in the visual editor.
- The read-only permissions required to monitor Route 53 Resolver are not present in the managed policy "ReadOnlyAccess". To monitor, construct a new policy from scratch in the visual editor or create a role with the necessary permissions.
These predefined policies are maintained and updated by the AWS team itself, so when we bring in monitoring support for any new AWS service, there won't be any need for you to update the permissions in the policy document.
The supported AWS services and the individual actions required for each service is mentioned below.
| AWS service | Read-level actions | Partial write-level actions |
|---|---|---|
| CloudWatch |
"cloudwatch:GetMetricData", |
|
| CloudWatch Logs |
"logs:Start*" |
|
| DynamoDB |
"dynamodb:DescribeTable", |
|
| EC2 |
"ec2:DescribeAddresses", |
"ec2:RebootInstances", |
| Elastic Beanstalk (EBS) |
"elasticbeanstalk:DescribeEnvironmentResources", |
"elasticbeanstalk:RestartAppServer" |
| ELB |
"elasticloadbalancing:DescribeLoadBalancers", |
|
| Gateway Load Balancer |
"elasticloadbalancing:DescribeLoadBalancers", |
|
| RDS |
"rds:ListTagsForResource", |
"rds:StartDBInstance", |
| S3 |
"s3:GetObjectAcl", |
|
| SNS |
"sns:ListSubscriptions", |
sns:Publish |
| Lambda |
"lambda:ListFunctions", |
"lambda:InvokeFunction" |
| Lambda logs | logs:Describe*, logs:Get* |
|
| Amazon Inspector | "inspector2:ListFindings" | |
| ElastiCache |
"elasticache:DescribeCacheClusters", |
elasticache:RebootCacheCluster |
| Simple Queue Service (SQS) |
"sqs:ListQueues", |
sqs:SendMessage |
| Amazon CloudFront |
"cloudfront:GetDistribution", |
|
| Amazon Kinesis Data Streams |
"kinesis:DescribeStreamSummary", |
kinesis:PutRecord" |
| Amazon Kinesis Video Streams |
"kinesisvideo:ListStreams", |
|
| Amazon Kinesis Firehose |
"firehose:ListDeliveryStreams", |
|
| Amazon Kinesis Data Analytics |
"kinesisanalytics:ListApplications", |
kinesisanalytics:StopApplication kinesisanalytics:StartApplication |
| Route 53 |
Route 53 Health Check: |
|
| Elastic Beanstalk |
"elasticbeanstalk:DescribeEnvironmentResources", |
"elasticbeanstalk:RestartAppServer" |
| Direct Connect |
"directconnect:DescribeConnections", |
|
| VPC-Virtual Private Network (VPN) connection |
"ec2:DescribeVpnConnections", |
|
| API Gateway | "apigateway:GET" | apigateway:POST |
| Amazon Elastic Container Service (ECS) |
"ecs:ListServices", |
|
| Amazon Redshift |
"redshift:DescribeClusters", |
redshift:RebootCluster |
| Elastic File System (EFS) |
"elasticfilesystem:DescribeFileSystems", |
|
| Simple Email Service (SES) |
"ses:DescribeConfigurationSet", |
ses:SendEmail |
| Step Functions |
"states:ListStateMachines", |
"states:StartExecution" |
| Web Application Firewall (WAF) |
"waf-regional:ListWebACLs", |
|
| Key Management Service (KMS) |
"kms:DescribeCustomKeyStores", |
|
| CloudSearch |
"cloudsearch:DescribeDomains", |
|
| Elasticsearch |
"es:DescribeElasticsearchDomain", |
|
| Elastic MapReduce |
"elasticmapreduce:ListSecurityConfigurations", |
elasticmapreduce:addJobFlowSteps |
| WorkSpaces |
"workspaces:DescribeTags", |
workspaces:StartWorkspaces workspaces:RebootWorkspaces workspaces:RebuildWorkspaces workspaces:StopWorkspaces |
| Certificate Manager (ACM) |
"acm:ListCertificates", |
|
| Lightsail Instance |
"lightsail:GetInstances", |
lightsail:StartInstance lightsail:StopInstance lightsail:RebootInstance |
| Lightsail Database |
"lightsail:GetRelationalDatabases", |
lightsail:StartRelationalDatabase lightsail:StopRelationalDatabase lightsail:RebootRelationalDatabase |
| Lightsail Load Balancer |
"lightsail:GetLoadBalancers", |
lightsail:StartRelationalDatabase lightsail:StopRelationalDatabase lightsail:RebootRelationalDatabase |
| Elastic Kubernetes Service (EKS) |
"eks:DescribeCluster", |
|
| Storage Gateway |
"storagegateway:DescribeGatewayInformation", |
|
| Amazon MQ |
"mq:DescribeBroker", |
mq:RebootBroker |
| Transit Gateway |
"ec2:DescribeTransitGatewayAttachments", |
ec2:SearchTransitGatewayRoutes ec2:SearchTransitGatewayMulticastGroups |
| Data Migration Service (DMS) |
"dms:DescribeAccountAttributes", |
dms:StartReplicationTask dms:StopReplicationTask |
| Amazon FSx |
"fsx:ListTagsForResource", "fsx:DescribeBackups", "fsx:DescribeDataRepositoryTasks", "fsx:DescribeFileSystems", "fsx:DescribeVolumes", "fsx:DescribeStorageVirtualMachines" |
fsx:CreateDataRepositoryTask fsx:CreateBackup |
| GuardDuty |
"guardduty:ListDetectors", |
|
| Lambda@Edge |
"lambda:GetAccountSettings", |
lambda:InvokeFunction |
| DocumentDB |
"rds:DescribeDBClusters", |
|
| Amazon Secure File Transfer Protocol (SFTP) |
"transfer:DescribeUser", |
|
| AWS Systems Manager |
"ssm:ListCommands", |
|
| Service Quotas |
"servicequotas:GetRequestedServiceQuotaChange", |
"servicequotas:RequestServiceQuotaIncrease" |
| Amazon AppStream 2.0 |
"appstream:DescribeFleets", |
"appstream:StopFleet" |
| AWS AppSync |
"Appsync:getGraphqlApi", |
|
| AWS Health |
"health:DescribeAffectedEntities", |
|
| AWS Backup |
"backup:ListCopyJobs", |
|
| Amazon EBS volume |
"ec2:DescribeVolumes" |
"ec2:DescribeVolumes" |
| AWS Batch |
"batch:DescribeJobDefinitions", |
"batch:TerminateJob" |
| Amazon EBS snapshot |
"ec2:DescribeVolumes", |
|
| AWS Secrets Manager |
"secretsmanager:DescribeSecret", |
"secretsmanager:RotateSecret" |
| AWS Elastic IP |
"ec2: describeAddresses", |
|
| AWS Trusted Advisor |
"support:DescribeTrustedAdvisorCheckResult", |
"support:RefreshTrustedAdvisorCheck" |
| Amazon VPC |
"ec2:Describe*" |
|
| Amazon RDS Proxy |
"rds:DescribeDBProxies", |
|
| Amazon MSK |
"kafka:ListClustersV2", |
|
| AWS Glue |
"glue:ListJobs", |
"glue:StartJobRun" "glue:StartCrawler" |
| RabbitMQ |
"mq:DescribeBroker", |
|
| AWS DRS |
"drs:DescribeSourceServers", |
|
| Amazon Cognito |
"cognito-idp:ListIdentityProviders", |
|
| AWS Organizations |
"organizations:ListRoots", |
|
| Amazon CloudWatch Logs |
"logs:GetDataProtectionPolicy", |
|
| AWS PrivateLink |
"ec2:Describe*”, |
|
| Amazon Elasticache Valkey |
"elasticache:DescribeServerlessCaches", "elasticache:DescribeCacheSubnetGroups", "elasticache:ListTagsForResource", "elasticache:DescribeCacheClusters", "elasticache:DescribeReplicationGroups", "elasticache:DescribeServerlessCacheSnapshots", "elasticache:DescribeSnapshots", "elasticache:DescribeEvents", "elasticache:DescribeUpdateActions" |
|
| Amazon Elastic Container Registry |
"ecr:DescribeRepositories", |
|
| Amazon DLM |
"dlm:GetLifecyclePolicies", |
Create your own custom IAM policy (Visual editor)
If your organization doesn't permit you to assign the default ReadOnly policy or if you prefer to have more precise control over the permissions you provide, you can create your own policy using the point-and-click visual editor in the IAM console.
Follow the steps mentioned below to create a new policy using the visual editor:
- Log in to the AWS IAM console.
- Select Access Management > Policies from the left navigation pane.
- Click Create policy.
- Select the Visual editor tab.
- Search and select CloudWatch from the Select a service drop-down list.
- From the Access level section, select Read. Select the applicable read actions.
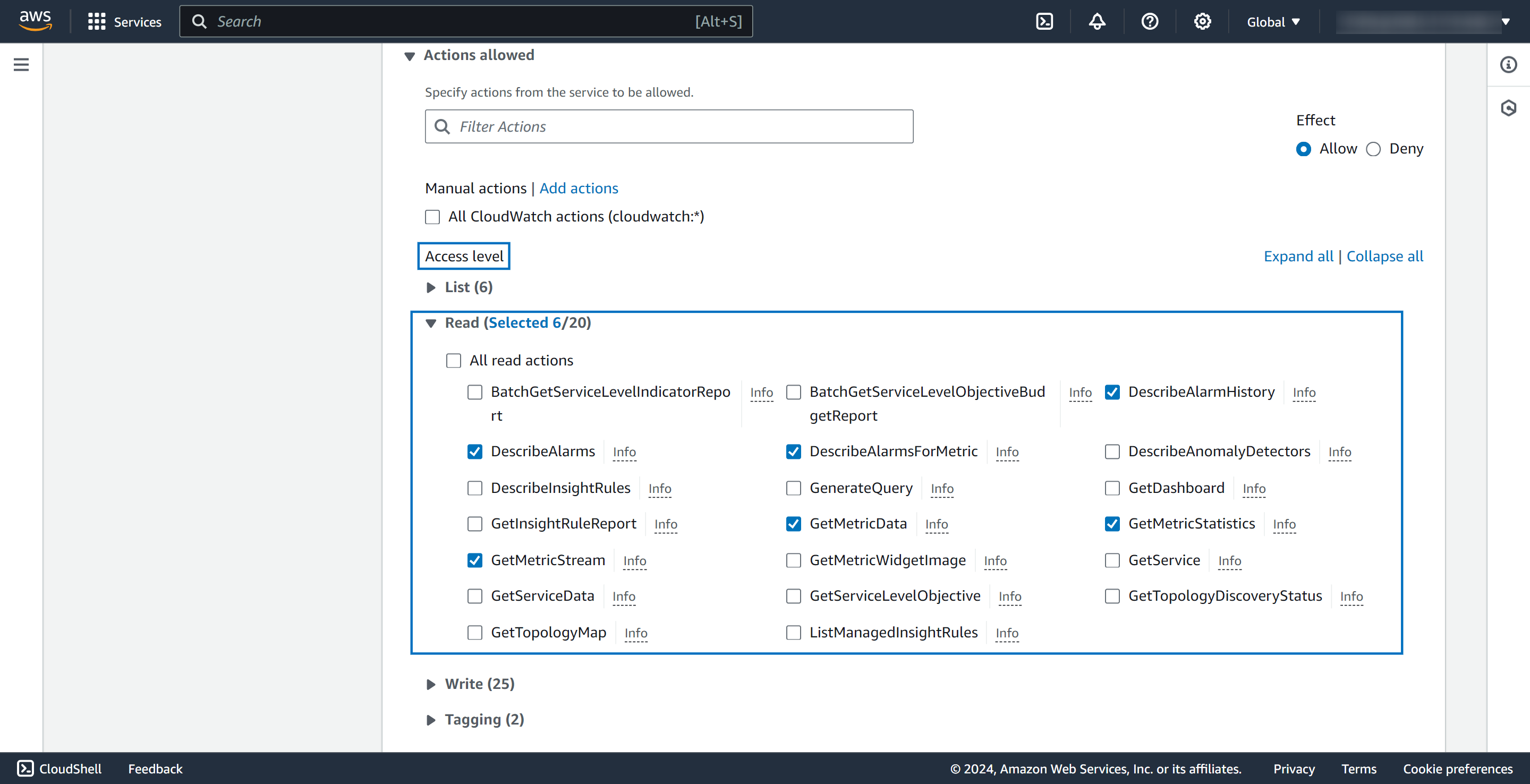
- Configure the Resources and Request conditions sections based on your requirement.
- Click +Add more permissions to continue the same process as above for other supported services as needed. Click Next once your have completed the configurations.
- In the Review and create page, enter the Policy name and Description.
- Click Create policy.
Site24x7's custom policy for ReadOnly actions (JSON)
You can also use our custom policy document to provide access to your AWS resources. Paste the policy JSON mentioned below in the JSON editor, review it, give an appropriate name and description and click on create policy.
Once done, attach the policy to the Site24x7 IAM user or role.
{
"Version":"2012-10-17",
"Statement":[
{
"Sid":"Statement1",
"Effect":"Allow",
"Action":[
"cloudwatch:Describe*",
"cloudwatch:Get*",
"cloudwatch:List*",
"dynamodb:Describe*",
"dynamodb:List*",
"ec2:Describe*",
"sqs:Get*",
"sqs:List*",
"autoscaling:Describe*",
"elasticloadbalancing:Describe*",
"cloudfront:Get*",
"cloudfront:List*",
"s3:Get*",
"s3:List*",
"rds:Describe*",
"rds:List*",
"kinesisanalytics:Describe*",
"kinesisanalytics:Get*",
"kinesisanalytics:List*",
"kinesis:Describe*",
"kinesis:Get*",
"kinesis:List*",
"kinesisvideo:Get*",
"kinesisvideo:List*",
"kinesisvideo:Describe*",
"firehose:Describe*",
"firehose:List*",
"elasticache:Describe*",
"elasticache:List*",
"elasticbeanstalk:Describe*",
"elasticbeanstalk:List*",
"directconnect:Describe*",
"apigateway:GET",
"ecs:DescribeServices",
"ecs:DescribeContainerInstances",
"ecs:DescribeClusters",
"redshift:Describe*",
"elasticfilesystem:Describe*",
"ses:Get*",
"ses:List*",
"ses:Describe*",
"lambda:List*",
"lambda:Get*",
"logs:Describe*",
"logs:Get*",
"route53domains:Get*",
"route53domains:List*",
"route53:Get*",
"route53:List*",
"route53resolver:Get*",
"route53resolver:List*",
"states:List*",
"states:Describe*",
"states:GetExecutionHistory",
"sns:Get*",
"sns:List*",
"kms:Describe*",
"kms:Get*",
"kms:List*",
"waf:Get*",
"waf:List*",
"waf-regional:List*",
"waf-regional:Get*",
"cloudsearch:Describe*",
"cloudsearch:List*",
"es:Describe*",
"es:List*",
"es:Get*",
"workspaces:Describe*",
"ds:Describe*",
"elasticmapreduce:List*",
"elasticmapreduce:Describe*",
"acm:GetCertificate",
"acm:Describe*",
"acm:List*",
"lightsail:Get*",
"eks:Describe*",
"eks:List*",
"mq:Describe*",
"mq:List*",
"ec2:Get*",
"ec2:SearchTransitGatewayRoutes",
"ec2:SearchTransitGatewayMulticastGroups",
"storagegateway:List*",
"storagegateway:Describe*",
"guardduty:GetFindings",
"guardduty:ListDetectors",
"guardduty:ListFindings",
"dms:Describe*",
"dms:List*",
"dms:TestConnection",
"fsx:Describe*",
"fsx:ListTagsForResource",
"inspector:List*",
"inspector:Describe*",
"transfer:Describe*",
"transfer:List*",
"ssm:ListCommands",
"ssm:DescribeInstanceInformation",
"ssm:ListCommandInvocations",
"glue:List*",
"glue:Get*",
"appstream:Describe*",
"appstream:List*",
"appsync:List*",
"appsync:Get*",
"health:Describe*",
"batch:Describe*",
"batch:List*",
"secretsmanager:DescribeSecret",
"secretsmanager:ListSecrets",
"secretsmanager:GetResourcePolicy",
"support:DescribeTrustedAdvisorCheckResult",
"support:DescribeTrustedAdvisorCheckSummaries",
"support:DescribeTrustedAdvisorChecks",
"kafka:ListClustersV2",
"kafka:Describe*",
"kafka:ListNodes",
"kafka:ListReplicators",
"kafkaconnect:List*",
"kafkaconnect:DescribeConnector",
"kafkaconnect:DescribeCustomPlugin",
"kafkaconnect:DescribeWorkerConfiguration",
"drs:Describe*",
"drs:List*",
"drs:Get*",
"cognito-idp:List*",
"cognito-idp:Describe*",
"cognito-identity:List*",
"cognito-identity:Describe*",
"cognito-identity:GetIdentityPoolRoles",
"logs:Start*",
"organizations:List*",
"organizations:Describe*",
"logs:List*",
"elasticache:DescribeServerlessCaches",
"elasticache:DescribeCacheSubnetGroups",
"elasticache:ListTagsForResource",
"elasticache:DescribeCacheClusters",
"elasticache:DescribeReplicationGroups",
"elasticache:DescribeServerlessCacheSnapshots",
"elasticache:DescribeSnapshots",
"elasticache:DescribeEvents",
"elasticache:DescribeUpdateActions",
"logs:GetDataProtectionPolicy",
"logs:DescribeLogGroups",
"logs:ListLogAnomalyDetectors",
"logs:DescribeLogStreams",
"logs:DescribeSubscriptionFilters",
"logs:GetLogEvents",
"logs:DescribeAccountPolicies",
"logs:DescribeMetricFilters",
"logs:DescribeFieldIndexes",
"logs:ListTagsForResource",
"dlm:GetLifecyclePolicies",
"dlm:GetLifecyclePolicy",
"ecr:DescribeRepositories",
"ecr:ListTagsForResource",
"ecr:DescribeImages",
"ecr:DescribeRegistry",
"ecr:DescribePullThroughCacheRules",
"ecr:GetRepositoryPolicy",
"ecr:GetLifecyclePolicy",
"ecr:GetLifecyclePolicyPreview",
"ecr-public:DescribeRepositories",
"ecr-public:DescribeImages",
"ecr-public:ListTagsForResource",
"ecr-public:GetRepositoryPolicy"
],
"Resource":[
"*"
]
}
]
}
This policy was last updated on November 11, 2025.
The policy is created and maintained by the Site24x7 team, and provide ReadOnly access to all the AWS services under monitoring support. Also, the policy is subject to change when new AWS integrations get added, so please make sure you are up to with the latest version.
Site24x7's custom policy for partial write-level actions (JSON)
Create a new custom IAM policy with the below mentioned JSON, to help Site24x7 perform actions in response to alert events.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:RebootInstances",
"sns:Publish",
"ec2:StartInstances",
"kinesisanalytics:StopApplication",
"kinesisanalytics:StartApplication",
"kinesis:PutRecord",
"rds:RebootDBInstance",
"elasticache:RebootCacheCluster",
"lambda:InvokeFunction",
"redshift:RebootCluster",
"ses:SendEmail",
"apigateway:POST",
"elasticbeanstalk:RestartAppServer",
"sqs:SendMessage",
"rds:StopDBInstance",
"ec2:StopInstances",
"rds:StartDBInstance",
"states:StartExecution",
"elasticmapreduce:addJobFlowSteps",
"workspaces:StartWorkspaces",
"workspaces:RebootWorkspaces",
"workspaces:RebuildWorkspaces",
"workspaces:StopWorkspaces",
"lightsail:StartRelationalDatabase",
"lightsail:StopRelationalDatabase",
"lightsail:RebootRelationalDatabase",
"lightsail:StartInstance",
"lightsail:StopInstance",
"lightsail:RebootInstance",
"mq:RebootBroker",
"dms:StartReplicationTask",
"dms:StopReplicationTask",
"fsx:CreateDataRepositoryTask",
"fsx:CreateBackup",
"transfer:StartServer",
"transfer:StopServer",
"servicequotas:RequestServiceQuotaIncrease",
"appstream:StopFleet",
"appstream:StartFleet",
"batch:TerminateJob",
"batch:CancelJob",
"secretsmanager:RotateSecret",
"support:RefreshTrustedAdvisorCheck",
"glue:StartJobRun",
"glue:StartCrawler"
],
"Resource": "*"
}
]
}
This policy was last updated on August 12, 2025.
The above policy JSON contains partial write-level permissions. These permissions are used for automations such as stop/start/reboot EC2 and RDS instances , reboot ElastiCache clusters , invoke Lambda functions , start/stop analytics application and publish message to SNS topic or SQS queue and many more. If you don't want Site24x7 to perform certain actions you can manually edit or remove the permission from the JSON.