Terraform for Site24x7
Terraform is an Infrastructure as Code tool that helps to create, edit, and manage cloud resources easily and efficiently. You can use Terraform to manage your Site24x7 resources through code by following some simple steps. You can add, update, or delete your resources, and handle administration-related updates in Site24x7 using Terraform.
Benefits of using Terraform
- Ensure error-free deployments
- Handle heterogeneous cloud deployments for fault tolerance
- Collaborate, obtain specific versions, and create your own environment
- Spawn and remove testing environments easily
- Improve deployment speeds
- Build, version, or change infrastructure safely and efficiently
- Trace and correct configuration-level issues
Supported resources in Site24x7
You can create, edit, or delete the following resources in Site24x7 by using Terraform:
- Website Monitor
- Web Transaction (Browser) Monitor
- DNS Server Monitor
- Port (Custom Protocol) Monitor
- Ping Monitor
- Web Page Speed (Browser) Monitor
- FTP Transfer Monitor
- ISP Monitor
- SSL Certificate Expiry Monitor
- Domain Expiry Monitor
- Rest API Monitor
- Server Monitor
- Heartbeat Monitor
- URL IT Automation
- Monitor Group
- Threshold Profile
- Location Profile
- Notification Profile
- User Group
- User
- Tags
- Schedule Maintenance
Integrations
Data sources
Steps to generate Site24x7 OAuth credentials
Site24x7 REST APIs use OAuth 2.0 protocol to authorize and authenticate calls. To generate Site24x7 OAuth credentials (SITE24X7_OAUTH2_CLIENT_ID, SITE24X7_OAUTH2_CLIENT_SECRET and SITE24X7_OAUTH2_REFRESH_TOKEN), please follow the following steps:
- Visit https://api-console.zoho.com/
- Choose the self client option.
- Copy the Client ID and Client Secret, and paste them in the curl command below.
- Copy the following and paste it in the scope field and click Create.
Site24x7.account.All,Site24x7.admin.All,Site24x7.reports.All,Site24x7.operations.All,Site24x7.msp.All,Site24x7.bu.All .
- Copy the generated code, paste it in the command below and execute the same.
curl
https://accounts.zoho.com/oauth/v2/token-X POST
-d "client_id=" -d "client_secret=" -d "code=" -d "grant_type=authorization_code" --insecure - The response for the command given above will be similar to the one given below.
{"access_token":"1000.dfsewerwe33.rterert23","refresh_token":"1000.abdfdf.32dsfsdf","token_type":"Bearer","expires_in":3600} - Copy the CLIENT_ID, CLIENT_SECRET, refresh_token and configure them in your terraform configuration file for the attributes oauth2_client_id, oauth2_client_secret, oauth2_refresh_token respectively.
Note: Domain names in the OAuth credentials generation steps vary based on your data centre.
- United States (US) - https://accounts.zoho.com and https://api-console.zoho.com
- Europe (EU) - https://accounts.zoho.eu and https://api-console.zoho.eu
- China (CN) - https://accounts.zoho.com.cn and https://api-console.zoho.com.cn
- India (IN) - https://accounts.zoho.in and https://api-console.zoho.in
- Australia (AU) - https://accounts.zoho.com.au and https://api-console.zoho.com.au
How to add Site24x7 resources using Terraform
Bootstrap Terraform and the Site24x7 provider
Add the content below to your Terraform configuration file to bootstrap Terraform and the Site24x7 provider.
terraform {
required_version = "~> 0.15.0"
required_providers {
site24x7 = {
source = "site24x7/site24x7"
version = "1.0.10"
}
}
}
Set your Site24x7 OAuth credentials in the bash environment
You need to export your Site24x7 OAuth credentials before applying your configuration. To do so, execute the following shell commands:
$ export
SITE24X7_OAUTH2_CLIENT_ID=""
$ export
SITE24X7_OAUTH2_CLIENT_SECRET=""
$ export
SITE24X7_OAUTH2_REFRESH_TOKEN=""
Configuring the Site24x7 provider in Terraform
You can use the following command to configure Site24x7 as a provider in Terraform:
provider "site24x7" {
data_center = "US"
retry_min_wait = 1
retry_max_wait = 30
max_retries = 4
}
data_center
Specify the data center for your account accordingly. For example, if your data center is in the United States, then your value will be data_center="US".
| Region | Data Center |
|---|---|
| United States (.com) | US |
| European Union (.eu) | EU |
| India (.in) | IN |
| Australia (.au) | AU |
| China (.cn) | CN |
oauth2_client_id
The client ID will be looked up in the SITE24X7_OAUTH2_CLIENT_ID environment variable if the attribute is empty.
oauth2_client_secret
The client secret will be looked up in the SITE24X7_OAUTH2_CLIENT_SECRET environment variable if the attribute is empty.
oauth2_refresh_token
The refresh token will be looked up in the SITE24X7_OAUTH2_REFRESH_TOKEN environment variable if the attribute is empty.
retry_min_wait
Specify the minimum wait time in seconds before retrying the failed Site24x7 API requests.
retry_max_wait
Specify the maximum wait time in seconds before retrying the failed Site24x7 API requests.
max_retries
Specify the maximum number of Site24x7 API request retries to be performed before aborting the action.
Creating a resource
By creating monitors in Site24x7, you can track the performance and metrics of your websites, infrastructure, and network devices.
For instance, to create a website monitor for your environment, you can paste the configuration below into your Terraform file:
{
display_name = "Example Monitor"
website = "https://www.example.com"
check_frequency = "1"
location_profile_name = "North America"
}
- The display name is the name you have to provide for your website monitor.
- The website is the URL that needs to be monitored.
- Check frequency stands for the frequency at which the polling should be conducted.
- The location profile is the location from where you'd like to monitor your resources. You can specify either location_profile_id or location_profile_name. If neither is specified, the first profile returned by the /api/location_profiles endpoint (https://www.site24x7.com/help/api/#list-of-all-location-profiles) will be used.
Applying the configuration in Terraform
You can execute the command terraform init to initialize the provider, and then execute terraform apply to apply the configuration defined in your Terraform file. Terraform will perform the following actions:
# site24x7_website_monitor.website_monitor_example will be created
+ resource "site24x7_website_monitor"
"website_monitor_example" {
+ check_frequency = "1"
+ display_name = "Example Monitor"
+ http_method = "G"
+ id = (will be known after applying)
+ location_profile_id = (will be known after applying)
+ location_profile_name = "North America"
+ match_regex_severity = 2
+ matching_keyword_severity = 2
+ notification_profile_id = (will be known after applying)
+ response_headers_severity = 2
+ tag_ids = (will be known after applying)
+ threshold_profile_id = (will be known after applying)
+ timeout = 10
+ unmatching_keyword_severity = 2
+ use_name_server = true
+ user_group_ids = (will be known after applying)
+ website = "https://www.example.com"
}
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
site24x7_website_monitor.website_monitor_example: Creating...
site24x7_website_monitor.website_monitor_example: Creation complete after 4s [id=306947000028195005]
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
Terraform will create the website monitor but change nothing else. Every Terraform apply configuration compares your template to the state of the resources that Terraform has handled previously. If this is the first Terraform configuration you're applying, it won't make any changes to the existing configurations.
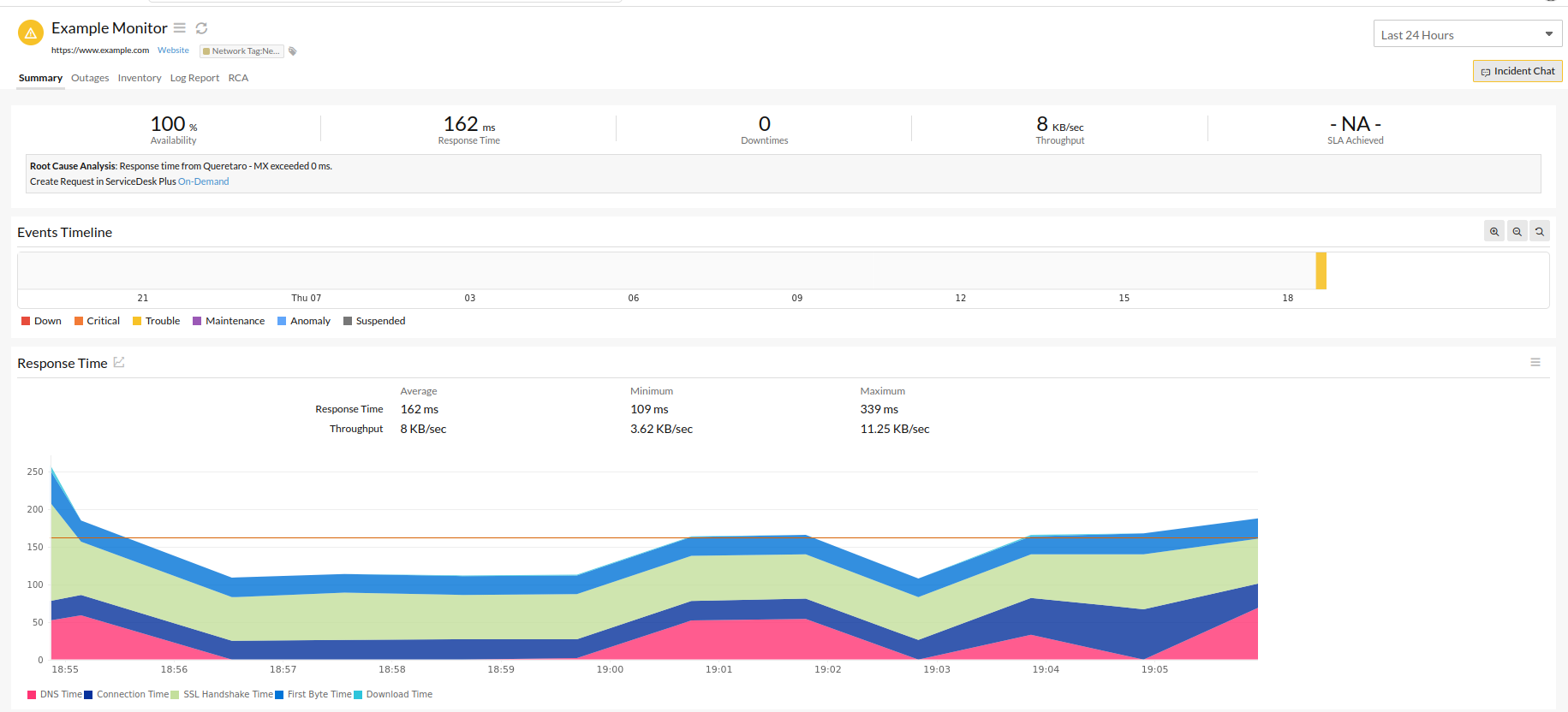
View the newly created monitor in Site24x7 by logging in to Site24x7 and navigating to Home > Monitors. Then, choose the monitor of your preference.
To import monitors and generate configurations, navigate to Github.
Please feel free to request support for features of your preference at Github or on the Site24x7 community forum.
- You can refer to the Github page for the complete list of resources we support.
- For provider documentation, refer Terraform Registry.